Apple recently updated its security support document to provide iPhone, iPad, and Mac users with enhanced guidelines on recognizing and avoiding social engineering schemes, such as phishing messages and fake support calls. This refresh comes in response to an increase in “smishing” attacks, where malicious actors send SMS messages attempting to steal Apple ID usernames and passwords via a fake iCloud website.
The updated guidelines emphasize the importance of ignoring suspicious messages and links. Apple reassures users that it will never ask for Apple ID passwords or verification codes, request users to log into a website, tap Accept in a two-factor authentication dialog, or disable security features like two-factor authentication, Find My, or Stolen Device Protection. Users are advised to contact Apple directly if they receive any suspicious communication purporting to be from the company.
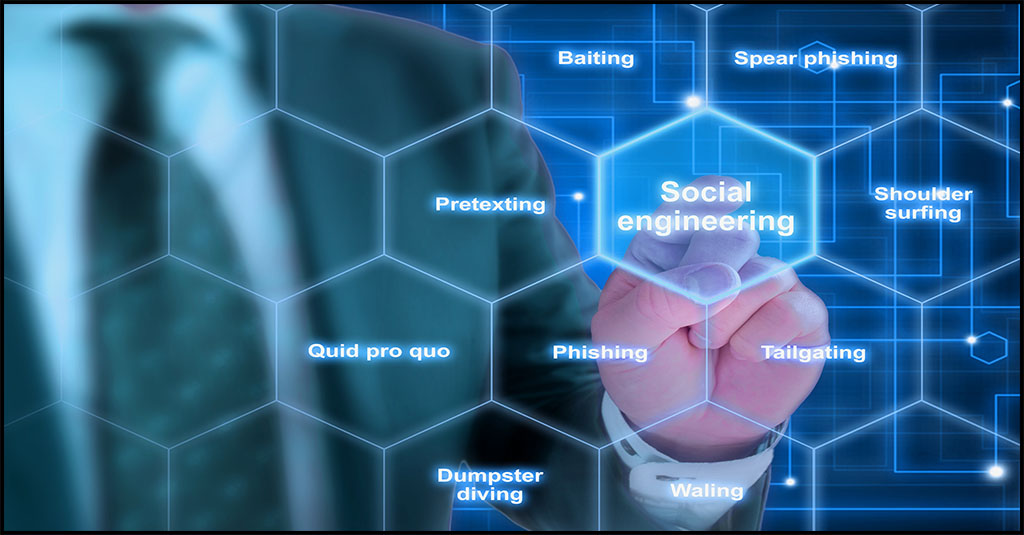
To further protect users, Apple provides several key security tips: never share personal data or security codes, keep Apple ID passwords and verification codes confidential, avoid using Apple Gift Cards for payments, and recognize legitimate Apple communications regarding App Store or iTunes Store purchases.
Users are also encouraged to download software only from trusted sources and avoid interacting with unsolicited or suspicious messages and calls.
Apple warns that scammers may use scare tactics, such as threatening stolen personal information or unauthorized charges, to create a sense of urgency. Users should be cautious of any login information or security code requests and avoid entering this information on websites accessed via links in texts or emails.
The company also advises against downloading unsafe software or configuration profiles and ignoring any pop-up instructions, recommending that users close the entire window or tab if such messages appear.
Additionally, Apple provides detailed instructions on how to spot social engineering schemes, the various forms these scams can take, and how to report suspicious emails, messages, and phone calls.
A separate support document outlines what to expect from genuine Apple Support interactions and clarifies the types of information Apple will never request, helping users distinguish legitimate communications from fraudulent ones.





Leave a Reply